
There are multiple ways in which hackers and cybercriminals can access your IT systems. One way often not considered involves “convincing” your employees to “give away” information. So, it doesn’t matter if you have the best security solutions in place, if your employees aren’t aware of such risks then unfortunately they can fall victim.
Human error has often been the root cause of security failures and other mishaps. The worst part is that human error is probably the easiest vulnerability to protect against. Hackers/cybercriminals are highly intelligent individuals and evidence of this lies in the fact that they have devised several clever and manipulative techniques to get people to do their dirty work.
One such technique involves the use of social engineering scams. Social engineering scams are scams wherein the target or victim is psychologically manipulated into giving away information or giving someone access to your system.
Here are some of the most common social engineering scams that your employees are likely to come across:
Phishing Scams
These are scam emails that appear to come from a service provider, and try and entice a user to give over information such as their user name and password. One such example appears from your email provider, so suggest your mailbox is full, or you account will be deleted, login here to avoid deletion. Here is an example we have seen recently:
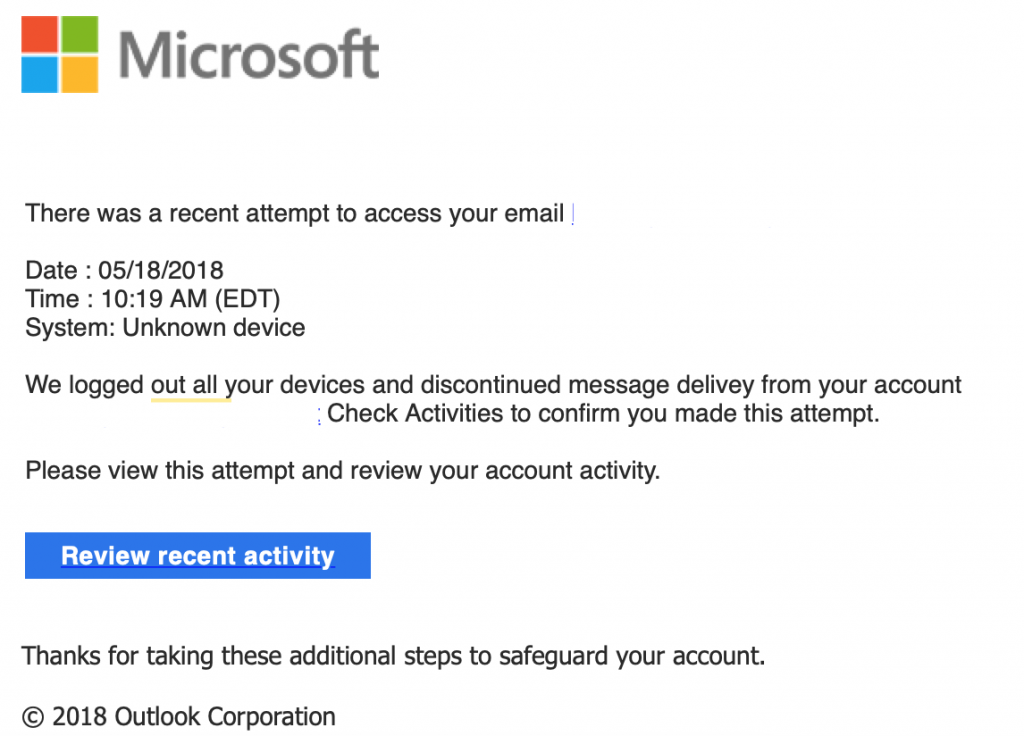
If you were to click the ‘Review recent activity’ button, it would take you to a spoof version of your email system to capture your login details.
Invoice fraud
ABC Ltd receive an email purporting to be from one of their customers or suppliers explaining that their bank details had changed and that any future invoices should be paid to the specified beneficiary account. When ABC Ltd received a genuine invoice via their customer for £200,000 to be paid to the supplier, they paid it to the fraudulent details. It only became apparent that it was a fraud when the genuine supplier called to ask why they have not received the funds. The genuine email from the supplier had been intercepted on route, the bank details changed and the email sent on.
Another example is an internal looking scam email from the a business owner telling a staff member to pay a particular person. These are surprisingly common, and due to information often available online via companies house its easy to find the owner of a business, and send a spoof email to your accounts email address is you have one.
Social media phishing
In this type of scam, cybercriminals use social media to target employees. They pretend to be legitimate contacts, such as a friend, colleague or a distant relative. The exact method involves sending a mail that draws in the target with a notification about their social media profile. The employee is then manipulated into logging in, which results in the login credentials being divulged.
Once the credentials are exposed, the hacker can use the information for all other accounts that respond to the same.
Prevention
As you can see there are a number of ways in which your users can fall victim to scams. Prevention is the best protection, next time you have a staff meeting perhaps its worth while having a 10 minuet chat to make everyone aware of these types of scams, particularly key staff members and staff that process payments. Some banks now offer tutorials to explain the risks to staff or why not ask your IT company in to advise your staff.

